

Cybersecurity Innovation Timeline
Cybersecurity Innovation Timeline
Sara Gilbert, Ph. D.
May 2, 2024
Biometric Authentication
Year invented: Technically, late 19th century
By: Alphonse Bertillon
Details:
1960s: semi-automated facial recognition methods were developed requiring administrators to analyze facial features within an image and extract usable feature points. Much more manual than the ones we can use to open out phones!
1969: fingerprint and facial recognition was so widely used in law enforcement, the FBI put funding towards developing automated processes. This was a catalyst for the development of more sophisticated sensors for biometric capture and data extraction.
1980s: the National Institute of Standards and Technology developed a Speech group to study and push forward the processes for speech recognition technology. These studies are the basis for the voice command and recognition systems we use today.
1985: the concept that much like fingerprints, irises, were unique to everyone was proposed and by 1994, the first iris recognition algorithm was patented. In addition, it was discovered that blood vessels patterns in eyes were unique to everyone and were used for authentication as well.
1991: facial detection technology was developed making real time recognition possible. While these processes had many faults, it skyrocketed interest in face recognition development.
2000s: hundreds of biometric authentication recognition algorithms were functional and patented within the USA. Biometrics were no longer being implemented in just large corporations or a government setting. They were sold in commercial products and were implemented at large scale events like the 2001 Super Bowl.
Souce: History of biometrics article
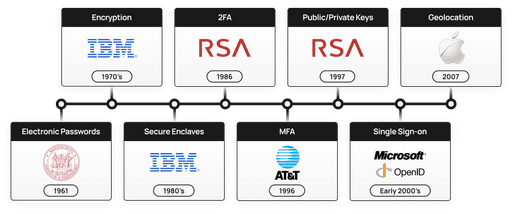
Electronic Passwords
Year invented: 1961
By: MIT professor Fernando Corbato
Details: “In 1961, MIT computer science professor Fernando Corbato created the first digital password as a project problem-solver. When he built a giant time-sharing computer, several users needed their own private access to the terminals. His solution? Give each user their own password.”
Source: Dashlane article
Encryption
Year invented: early 1970s
By: IBM
Details: IBM created a “crypto group” which designed a block cypher to protect customer data. This was adopted as the US standard in 1973 and remained in use until 1997.
Source: Thales article
Public / Private Keys
Year invented: 1976
By: Whitfield Diffie and Martin Hellman
Details:
1976: Whitfield Diffie and Martin Hellman published a research paper on what would be defined as the Diffie-Hellman key exchange. The code key was no longer pre-arranged for the first time, but a pair of keys (one public, one private but mathematically linked) was dynamically created for every correspondent.
1997 implemented by RSA
2000s: the Advanced Encryption Standard replaces DES, or AES (asymmetric key - the user and sender must know the same secret key), found through a competition open to the public. Today, AES is royalty-free worldwide and approved for use in classified US government information.
2005: Elliptic-curve cryptography (ECC) is an advanced public-key cryptography scheme that allows shorter encryption keys. Elliptic curve cryptosystems are more challenging to break than RSA and Diffie-Hellman.
Source: Thales article
Geolocation
Year invented: 1970s (US government only), implemented in 1995 (car GPS systems), cell phones in early 2000s
By: NAVSTAR
Details:
2000s: geolocation was integrated into another widely used technology that millions of people use daily: smartphone map applications. The history of map applications commenced with the first digital computer maps. ESRI (Environmental Systems Research Institute) was the pioneering company that made significant developments in this area.
2007: Apple released the first mobile device with assisted GPS location featuring Google Maps. This marked a significant milestone in the widespread availability of geolocation; from that point onwards, everyone could find their current location by clicking a few times on their phones.
Source: wikipedia and this geolocation history article
2FA
Year invented: 1986
By: RSA
Details: “Though there have been several predecessors to the modern day two-factor authentication system, the 2FA that we would recognize today was first made commercially available by the RSA company as a key fob in 1986. The fob had a small LCD screen that displayed a short numerical code which users appended to their passwords. For over 20 years, many large enterprises and governments made use of this type of extra protection for their internal systems. However, it would not become a common feature on the internet until this decade, after the number of people using account-based services—and the number of those accounts being hacked—hit critical mass.
Source: New America Case Study
Secure Enclaves
Year invented: 1980s, Apple iPhone implementation in 2014
By: US Government / IBM
Details: “They were planted as early as the 1980s in the hardware-based security research field. One of the earliest examples of Confidential Computing was the development of the secure kernel, a protected area of memory that can only be accessed by authorized code. The US government funded research and the Kernelized Secure Operating System was born. Secure co-processors were also already being developed by IBM to ensure data confidentiality and integrity, but it wasn't until recent years that the vision of Confidential Computing started to crystallize fully.”
Source: This blog post
Multifactor Authentication (mobile)
Year invented: 1996
By: AT&T
Details: “Kim Dotcom claims to have invented two-factor authentication back in 1997 when he was awarded a patent for his “method for authorizing in data transmission systems employing a transaction authorization number or a comparable password.” However, AT&T’s patent precedes Kim’s, having been granted a couple of years earlier in 1995. Regardless of who invented MFA, authentication is becoming more and more popular and affordable. In an age of data breaches, people should be given the opportunity to use it in order to secure their accounts.“
Source: TypingDNA article
Single Sign-on
Year invented: early 2000s
By: Microsoft / OpenID
Details:
2000s: “While it wasn’t called SSO in the early days, Microsoft created AD which allowed users to simply log in to their Windows devices and subsequently be able to access anything on their network that was Windows-based. However, as web applications emerged in the early 2000s, another generation of SSO solutions emerged to help users authenticate to non-Windows-based resources — these solutions are often referred to as IDaaS or Identity-as-a-Service.“
2005: “This is a decentralized identity system, but one that's actually decentralized and doesn't entirely crumble if one company turns evil or goes out of business. An OpenID identity is just a URL. You can have multiple identities in the same way you can have multiple URLs. All OpenID does is provide a way to prove that you own a URL (identity). And it does this without passing around your password, your email address, or anything you don't want it to. There's no profile exchange component at all: your profile is your identity URL, but recipients of your identity can then learn more about you from any public, semantically interesting documents linked thereunder (FOAF, RSS, Atom, vCARD, etc.).Anybody can run their own site using OpenID, and anybody can be an OpenID server, and they all work with each other without having to register with or pay anybody to "get started". An owner of a URL can pick which OpenID server to use. While nothing in the protocol requires JavaScript or modern browsers, the authentication scheme plays nicely with "AJAX"-style setups, so you can prove your identity to a site without bouncing between pages.”
Source: JumpCloud article and this livejournal (talk about a throwback) blog post
Blockchain
Year invented: Theoretically: 1991. In practice: 2009
By: Theory: Haber & Stornetta. In practice: Satoshi Nakamoto (as part of Bitcoin)
Details:
1991: Researcher scientists named Stuart Haber and W. Scott Stornetta introduced Blockchain Technology. These scientists wanted some Computational practical Solution for time-stamping the digital documents so that they couldn’t be tempered or misdated. So both scientists together developed a system with the help of Cryptography. In this System, the time-stamped documents are stored in a Chain of Blocks.
1992: Merkle Trees formed a legal corporation by using a system developed by Stuart Haber and W. Scott Stornetta with some more features. Hence, Blockchain Technology became efficient to store several documents to be collected into one block. Merkle used a Secured Chain of Blocks that stores multiple data records in a sequence. However, this technology became unused when the Patent came into existence in 2004.
2000: Stefan Konst published his theory of cryptographic secured chains, plus ideas for implementation.
2004: Cryptographic activist Hal Finney introduced a system for digital cash known as “Reusable Proof of Work”. This step was the game-changer in the history of Blockchain and Cryptography. This System helps others to solve the Double Spending Problem by keeping the ownership of tokens registered on a trusted server.
2008: Satoshi Nakamoto conceptualized the concept of “Distributed Blockchain” in his white paper: “A Peer to Peer Electronic Cash System”. He modified the model of Merkle Tree and created a system that is more secure and contains the secure history of data exchange. His System follows a peer-to-peer network of time stamping. His system became so useful that Cryptography became the backbone of Blockchain.
2009: The evolution of Blockchain is steady and promising and has become a need in various fields. In 2009, Satoshi Nakamoto released the Bitcoin White Paper. Blockchain technology is so secure that the following surprising news will give proof of that. A person named James Howells was an IT worker in the United Kingdom, he started mining bitcoins which are part of Blockchain in 2009 and stopped this in 2013. He spends $17,000 on it and after he stopped he sells the parts of his laptop on eBay and keep the drive with him so that when he needs to work again on bitcoin he will utilize it but while cleaning his house in 2013, he thrashed his drive with garbage and now his bitcoins cost nearly $127 million. This money now remains unclaimed in the Bitcoin system.
2014: The year 2014 is marked as the turning point for blockchain technology. Blockchain technology is separated from the currency and Blockchain 2.0 is born. Financial institutions and other industries started shifting their focus from digital currency to the development of blockchain technologies.
Source: This timeline
Biometric Authentication
Year invented: Technically, late 19th century
By: Alphonse Bertillon
Details:
1960s: semi-automated facial recognition methods were developed requiring administrators to analyze facial features within an image and extract usable feature points. Much more manual than the ones we can use to open out phones!
1969: fingerprint and facial recognition was so widely used in law enforcement, the FBI put funding towards developing automated processes. This was a catalyst for the development of more sophisticated sensors for biometric capture and data extraction.
1980s: the National Institute of Standards and Technology developed a Speech group to study and push forward the processes for speech recognition technology. These studies are the basis for the voice command and recognition systems we use today.
1985: the concept that much like fingerprints, irises, were unique to everyone was proposed and by 1994, the first iris recognition algorithm was patented. In addition, it was discovered that blood vessels patterns in eyes were unique to everyone and were used for authentication as well.
1991: facial detection technology was developed making real time recognition possible. While these processes had many faults, it skyrocketed interest in face recognition development.
2000s: hundreds of biometric authentication recognition algorithms were functional and patented within the USA. Biometrics were no longer being implemented in just large corporations or a government setting. They were sold in commercial products and were implemented at large scale events like the 2001 Super Bowl.
Souce: History of biometrics article
Electronic Passwords
Year invented: 1961
By: MIT professor Fernando Corbato
Details: “In 1961, MIT computer science professor Fernando Corbato created the first digital password as a project problem-solver. When he built a giant time-sharing computer, several users needed their own private access to the terminals. His solution? Give each user their own password.”
Source: Dashlane article
Encryption
Year invented: early 1970s
By: IBM
Details: IBM created a “crypto group” which designed a block cypher to protect customer data. This was adopted as the US standard in 1973 and remained in use until 1997.
Source: Thales article
Public / Private Keys
Year invented: 1976
By: Whitfield Diffie and Martin Hellman
Details:
1976: Whitfield Diffie and Martin Hellman published a research paper on what would be defined as the Diffie-Hellman key exchange. The code key was no longer pre-arranged for the first time, but a pair of keys (one public, one private but mathematically linked) was dynamically created for every correspondent.
1997 implemented by RSA
2000s: the Advanced Encryption Standard replaces DES, or AES (asymmetric key - the user and sender must know the same secret key), found through a competition open to the public. Today, AES is royalty-free worldwide and approved for use in classified US government information.
2005: Elliptic-curve cryptography (ECC) is an advanced public-key cryptography scheme that allows shorter encryption keys. Elliptic curve cryptosystems are more challenging to break than RSA and Diffie-Hellman.
Source: Thales article
Geolocation
Year invented: 1970s (US government only), implemented in 1995 (car GPS systems), cell phones in early 2000s
By: NAVSTAR
Details:
2000s: geolocation was integrated into another widely used technology that millions of people use daily: smartphone map applications. The history of map applications commenced with the first digital computer maps. ESRI (Environmental Systems Research Institute) was the pioneering company that made significant developments in this area.
2007: Apple released the first mobile device with assisted GPS location featuring Google Maps. This marked a significant milestone in the widespread availability of geolocation; from that point onwards, everyone could find their current location by clicking a few times on their phones.
Source: wikipedia and this geolocation history article
2FA
Year invented: 1986
By: RSA
Details:
“Though there have been several predecessors to the modern day two-factor authentication system, the 2FA that we would recognize today was first made commercially available by the RSA company as a key fob in 1986. The fob had a small LCD screen that displayed a short numerical code which users appended to their passwords. For over 20 years, many large enterprises and governments made use of this type of extra protection for their internal systems. However, it would not become a common feature on the internet until this decade, after the number of people using account-based services—and the number of those accounts being hacked—hit critical mass.
Source: New America Case Study
Secure Enclaves
Year invented: 1980s, Apple iPhone implementation in 2014
By: US Government / IBM
Details: “They were planted as early as the 1980s in the hardware-based security research field. One of the earliest examples of Confidential Computing was the development of the secure kernel, a protected area of memory that can only be accessed by authorized code. The US government funded research and the Kernelized Secure Operating System was born. Secure co-processors were also already being developed by IBM to ensure data confidentiality and integrity, but it wasn't until recent years that the vision of Confidential Computing started to crystallize fully.”
Source: This blog post
Multifactor Authentication (mobile)
Year invented: 1996
By: AT&T
Details: “Kim Dotcom claims to have invented two-factor authentication back in 1997 when he was awarded a patent for his “method for authorizing in data transmission systems employing a transaction authorization number or a comparable password.” However, AT&T’s patent precedes Kim’s, having been granted a couple of years earlier in 1995. Regardless of who invented MFA, authentication is becoming more and more popular and affordable. In an age of data breaches, people should be given the opportunity to use it in order to secure their accounts.“
Source: TypingDNA article
Single Sign-on
Year invented: early 2000s
By: Microsoft / OpenID
Details:
2000s: “While it wasn’t called SSO in the early days, Microsoft created AD which allowed users to simply log in to their Windows devices and subsequently be able to access anything on their network that was Windows-based. However, as web applications emerged in the early 2000s, another generation of SSO solutions emerged to help users authenticate to non-Windows-based resources — these solutions are often referred to as IDaaS or Identity-as-a-Service.“
2005: “This is a decentralized identity system, but one that's actually decentralized and doesn't entirely crumble if one company turns evil or goes out of business. An OpenID identity is just a URL. You can have multiple identities in the same way you can have multiple URLs. All OpenID does is provide a way to prove that you own a URL (identity). And it does this without passing around your password, your email address, or anything you don't want it to. There's no profile exchange component at all: your profile is your identity URL, but recipients of your identity can then learn more about you from any public, semantically interesting documents linked thereunder (FOAF, RSS, Atom, vCARD, etc.).Anybody can run their own site using OpenID, and anybody can be an OpenID server, and they all work with each other without having to register with or pay anybody to "get started". An owner of a URL can pick which OpenID server to use. While nothing in the protocol requires JavaScript or modern browsers, the authentication scheme plays nicely with "AJAX"-style setups, so you can prove your identity to a site without bouncing between pages.”
Source: JumpCloud article and this livejournal (talk about a throwback) blog post
Blockchain
Year invented: Theoretically: 1991. In practice: 2009
By: Theory: Haber & Stornetta. In practice: Satoshi Nakamoto (as part of Bitcoin)
Details:
1991: Researcher scientists named Stuart Haber and W. Scott Stornetta introduced Blockchain Technology. These scientists wanted some Computational practical Solution for time-stamping the digital documents so that they couldn’t be tempered or misdated. So both scientists together developed a system with the help of Cryptography. In this System, the time-stamped documents are stored in a Chain of Blocks.
1992: Merkle Trees formed a legal corporation by using a system developed by Stuart Haber and W. Scott Stornetta with some more features. Hence, Blockchain Technology became efficient to store several documents to be collected into one block. Merkle used a Secured Chain of Blocks that stores multiple data records in a sequence. However, this technology became unused when the Patent came into existence in 2004.
2000: Stefan Konst published his theory of cryptographic secured chains, plus ideas for implementation.
2004: Cryptographic activist Hal Finney introduced a system for digital cash known as “Reusable Proof of Work”. This step was the game-changer in the history of Blockchain and Cryptography. This System helps others to solve the Double Spending Problem by keeping the ownership of tokens registered on a trusted server.
2008: Satoshi Nakamoto conceptualized the concept of “Distributed Blockchain” in his white paper: “A Peer to Peer Electronic Cash System”. He modified the model of Merkle Tree and created a system that is more secure and contains the secure history of data exchange. His System follows a peer-to-peer network of time stamping. His system became so useful that Cryptography became the backbone of Blockchain.
2009: The evolution of Blockchain is steady and promising and has become a need in various fields. In 2009, Satoshi Nakamoto released the Bitcoin White Paper. Blockchain technology is so secure that the following surprising news will give proof of that. A person named James Howells was an IT worker in the United Kingdom, he started mining bitcoins which are part of Blockchain in 2009 and stopped this in 2013. He spends $17,000 on it and after he stopped he sells the parts of his laptop on eBay and keep the drive with him so that when he needs to work again on bitcoin he will utilize it but while cleaning his house in 2013, he thrashed his drive with garbage and now his bitcoins cost nearly $127 million. This money now remains unclaimed in the Bitcoin system.
2014: The year 2014 is marked as the turning point for blockchain technology. Blockchain technology is separated from the currency and Blockchain 2.0 is born. Financial institutions and other industries started shifting their focus from digital currency to the development of blockchain technologies.
Source: This timeline
© 2024 Fr0ntierX Inc. All rights reserved. Janus, Polaris, and the Janus and Polaris logos are trademarks of Fr0ntierX Inc.
© 2024 Fr0ntierX Inc. All rights reserved. Janus, Polaris, and the Janus and Polaris logos are trademarks of Fr0ntierX Inc.